The news that Volkswagen, which is the second largest automobile manufacturer and owns luxury brands like Audi, Bentley, Bugatti, Lamborghini and Porsche is involved in fidgeting its emission control system to deceive regulator is appalling.
Volkswagen has been accused of planting software in its popular diesel cars Audi A3, VW Beetle, VW Jetta, VW, Passat and VW Golf which automatically senses if the car is subject to emission testing. As soon as the software senses that the car is undergoing an emission test, it turns on emission control, helping the car to pass the emission test. And deviously, when it notices that the emission test is over and the car is operating in normal condition, it turns off the emission control, which makes its car spew out as much as 40 times the level of pollutants allowed under clean air rules by U.S. environmental Protection Agency (E.P.A).
This is plain fraud, a gross misrepresentation, and a scam which plays havoc with people’s health. It is not clear if the software has been planted in the cars sold in U.S only or to all the countries where these cars are being currently sold. Interestingly, if it becomes clear that the cars do not have the software in other countries where emission control norms are not as stringent as in U.S., it will be apparent that this fraud has been done with due care and with knowledge of senior management.
Consequently, Volkswagen now faces a huge penalty of up to $8 billion which is roughly 70% of its yearly profit of $12.3 billion. This is a huge cost that the shareholders will have to bear for the decisions that the Volkswagen top management undertook, all the while claiming to be “decreasing emissions one tree at a time” and claiming to be technologically advanced and responsible towards environment protection through “Think Blue”.
Why did Volkswagen cheat
Volkswagen is the second largest automobile manufacturer in the world and it aims to become number one. To become number one player in the automobile industry, it needs to be amongst the top 3 auto companies in U.S., the second largest market in the world after China.
Volkswagen has not been able to make a cut in the U.S. market and is presently number four behind Ford, General Motors and Toyota. Martin Winterkorn the Chairman of Volkswagen laid out in 2007, a plan to surpass both General Motors and Toyota and become the largest automobile maker in the world. For this plan to succeed, Volkswagen needed to sell three times as many cars in U.S. as it sold in 2008. This was a very ambitious target.
To crack the tough U.S diesel car market which has one of the stiffest of emission norms, it chose a shortcut rather than doing research and development and coming up with better engines for its cars.
What went wrong
This fraud points towards how weak company’s controls are, and the huge implications related to company’s claimed compliance with Germany’s KonTraG- A German law for Controls and Transparency. As per Volkswagen’s annual report for 2013, company’s Early Warning System (EWS) are in line with the requirements of the Gesetz zur kontrolle und Transparenz im Unternehmensbereich (KonTraG) and meets its requirement.
What is Internal Control
Internal control is a process, effected by an entity’s board of directors, management and other personnel, designed to reasonably manage risk affecting the achievement of objectives in the following categories:
- Effectiveness, efficiency, economy and accuracy of operations;
- Reliability and relevance of reporting; and
- Compliance with applicable laws and regulations
Importance of strong internal controls is not just confined to Banking and insurance industry, but is related to all types of organizations be it pharmaceutical company, a supermarket, an e-commerce company, a NGO, a government department or even a small neighborhood store. The level of complexity and sophistication is what changes when we talk about internal controls across industries, scale of operations and geographies.
Enron, Worldcom, Banco Espirito Santo (BES), Lehman Brothers, Arthur Anderson, Barings Bank, Satyam Computers, Seibu Railway’s Co., Kanebo Ltd., have one thing in common-weak internal controls. These high level accounting frauds, excessive and uncontrolled risk taking, weak governance, some of which resulted into total organization collapse, made governments, regulators, corporations and the shareholders particularly concerned about internal controls.
Realizing its importance most of the major economies of the world have specialized law which mandates a strong internal control for organizations. Sarbanes-Oxley Act of 2002 in U.S., Companies (Audit, Investigations and Community Enterprise) Act 2004 in U.K., Indian Company’s Act 2013 in India, financial Instruments and Exchange Act (J-SOX) in Japan, String Economy Act (C-SOX) in Cananda, KonTraG in Germany are the laws enacted in the respective countries to make sure governance and internal controls are robust and interest of shareholders, employees and general public are safeguarded.
Frameworks for Internal Control
To have strong and watertight internal controls, we have some very good internal control frameworks and these are all globally recognized. These are:
- COSO framework developed in United States by Committee of Sponsoring Organizations of Treadway Commission;
- The Turnbull Guidance of directors on U.K’s Combined Code on Corporate governance; and
- COCO Framework developed by Criteria of Control Board, Canada
Out of these, COSO framework is the most widely known and followed world over. Interestingly, even Volkswagen follows COSO’s framework for its risk management.
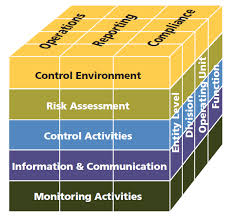
COSO is based on five components which are like foundation with 17 principles defining these components. These five components are:
- Control Environment
- Risk Assessment
- Control Activities
- Information & Communication
- Monitoring Activities
COSO & Volkswagen: Possible weak areas
|
S.N
|
COSO’s Components |
Volkswagen
|
| 1. |
Control Environment
The first component is all about setting the tone at the top; establishes expected standards of conduct and reinforces expectations. Standards, procedures, processes and the structures are defined for setting up internal controls. Importance of ethics and integrity are percolated down from top to bottom. |
This is possibly where the origin of weak controls lies. When the tone from the top is not able to assert that achieving the largest market share and becoming the largest automobile company in the world is to be achieved without sacrificing ethical standards and compromising integrity of organization. |
| 2. |
Risk Assessment
Objectives are set for each line of function so that it is clear to all the employees what is the end state that the organization is seeking to achieve. Keeping these objectives in mind, risks are assessed continually and a culture is driven across all the lines of function which makes it a habit with the employees to identify and assess the risks on periodic basis. |
Risks of losing face and damaging the reputation are one of the biggest stumbling blocks in achieving the objectives of becoming the largest car maker. Customers who can afford cars are also aware about environmental concerns and when these customers get to know that VW has adopted fraudulent practices, the acceptance of brand goes for a toss. In the highly competitive automobile industry, brand associations are very important. Customer would never want to drive a car which employs dubious policies and fools even government regulators. What is the proof that company is not duping its customers as well? |
| 3 |
Control Activities
These are the actions which help ensure that the risks are managed to achieve the objectives set earlier and in line with the tone from the Top. Control activities can be preventive or detective, or manual or automated. Control activities also include segregation of duties, periodic reviews, authorization matrices etc. |
It seems the risks of being seen on the wrong side of law were not assessed. Or possibly, if they were assessed, the mitigants could have been weak detection capabilities at E.P.A and rightly so, it took years to detect these devious means adopted by one of the most respected car makers of the world. Volkswagen may have believed that E.P.A will never be able to detect this software. |
| 4 |
Information & Communication
Information is the thread which keeps the five components of internal control bonded together. Information between various stakeholders, inter group, intra group, top to down, bottom to top is very critical in ensuring robust internal controls. |
Information and communication is important and helps to plug such illegal acts within an organization, provided, information flows freely from top to bottom and vice versa. |
| 5 |
Monitoring Activities
These are periodic reviews to ascertain whether components of internal controls are all functioning and producing desired controls. These reviews can be on-going or periodic with a defined frequency. These result in feedback mechanisms to all the stakeholders on status of internal controls. |
Monitoring activities clearly have failed to bring this risk up and flag off at senior most level. Only investigations will be able to reveal if senior management had taken a call to ignore this risk and were aware of this risk all along. |
Conclusion
Every time we read the annual reports of these large corporations, we get an assurance from the auditors that the internal controls of the company’s are strong and everything is hunky-dory, but still every now and then we get to hear news pertaining to large corporations like Toshiba in July 2015 and now this latest fraud involving Volkswagen deceiving environmental regulator.
Auditors will need to sharpen their skills and need to be updated about latest technologies including software capabilities which can be hiding in key components and other such modern warfare that executives use to fool governments, regulators, shareholders and also fellow employees.
Strong internal controls help everyone-executives and senior management in achieving their ambitious objectives is sustainable manner, it helps to instil faith in shareholders and regulators about the companies and they in turn listen to industry’s and top management’s genuine constraints and challenges, and finally it helps the customers as well when they purchase company’s products with a confidence that the company has high ethical standards and un-blemished integrity.